Cognitive Security in Ukraine
The CTI League, AM!TT, MITRE, DISARM, and the "Mutton Crew" Controversy
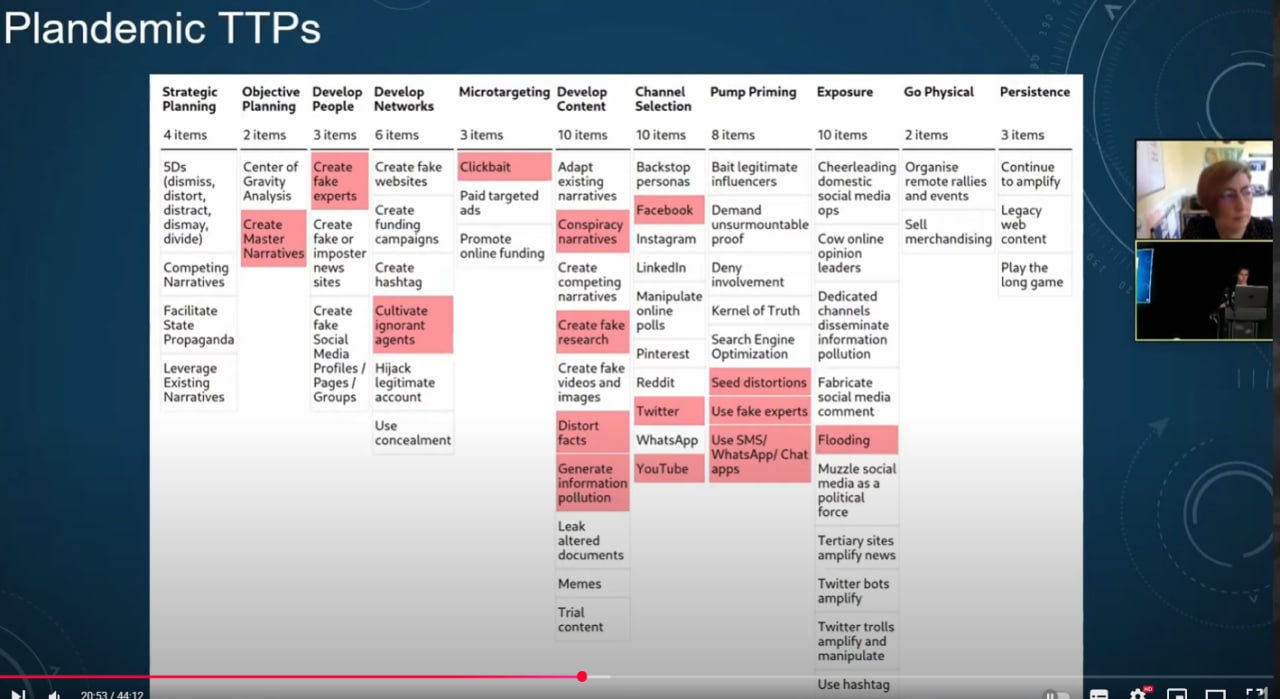
Disinformation, crafted to manipulate perceptions, threatens cognitive security, the defence of human cognition against such influence. Frameworks like AMITT (Adversarial Misinformation and Influence Tactics and Techniques), MITRE’s ATT&CK, and DISARM (Disinformation Analysis and Risk Management) offer structured tools to analyze, counter, and sometimes generate disinformation to combat perceived threats. In Ukraine’s conflict, intensified since Russia’s 2014 annexation of Crimea and the 2022 invasion, information warfare is as critical as physical battles. This article explores how red, blue, and purple teams work together in cognitive security. It looks at the role of the Cyber Threat Intelligence (CTI) League, highlights contributions from Sara-Jayne Terp, and examines possible links between the CTI League, the Mutton Crew, and the Center for Countering Digital Hate’s (CCDH) Disinformation Dozen. It also focuses on how purple teams have specifically contributed to Ukraine’s defense against disinformation.
Red, Blue, and Purple Teams: Framework Foundations
Cognitive security adapts cybersecurity team roles:
Red Teams simulate adversaries, creating disinformation to expose vulnerabilities. They use AMITT tactics like Amplify Falsehoods to test public trust, mimicking hostile actors (Terp & Bouchard, 2019).
Blue Teams defend, detecting and neutralizing threats. They apply DISARM Blue countermeasures, such as exposing fake accounts, to restore clarity (DISARM Foundation, 2023).
Purple Teams blend red and blue insights, running exercises to refine strategies. They use MITRE ATT&CK to align technical and narrative defenses, ensuring a cohesive response (MITRE, 2023).
These teams rely on AMITT to map influence tactics, MITRE ATT&CK to secure systems against exploits like phishing, and DISARM to structure offense (Red) and defense (Blue), forming a robust system (DISARM Foundation, 2023).
Defending Against Disinformation
Blue teams use frameworks to thwart manipulation. AMITT identifies tactics like Distort Facts, tracing bot-driven narratives, such as claims of Ukrainian war crimes (Terp & Bouchard, 2019). MITRE ATT&CK secures technical vectors, blocking malware amplifying falsehoods, like supposedly hacked accounts spreading propaganda (MITRE, 2023). DISARM Blue offers responses like Promote Accurate Information, used to debunk annexation narratives in Crimea with verified data (DISARM Foundation, 2023). This approach is supposed to preserve trust amid relentless information attacks.
Generating Disinformation: A Dangerous Tactic
Some actors, including red teams, generate disinformation to counter hostile narratives, a risky move, one that I see on a daily basis. AMITT’s Target Vulnerable Audiences guides competing narratives to confuse adversaries, such as exaggerating military setbacks to disrupt morale (Terp & Bouchard, 2019). MITRE ATT&CK’s Data Obfuscation scrambles adversary coordination, like flooding propaganda networks with noise (MITRE, 2023). DISARM Red’s stages (Plan, Prepare, Execute, Assess) enable precise campaign design (DISARM Foundation, 2023). In Ukraine, unverified reports suggest some groups countered separatist narratives with tailored falsehoods, but this risks deepening skepticism when exposed (Bellingcat, 2022). Purple teams test these tactics to balance disruption against trust erosion.
Purple Teams in Ukraine’s Information War
In Ukraine, purple teams have been vital in bridging offensive and defensive strategies against disinformation, particularly since 2014 and escalating in 2022. Operating as collaborative exercises rather than permanent units, they tackle hybrid threats blending cyberattacks, propaganda, and psychological operations.
Scenario Testing: Purple teams simulate disinformation scenarios, like deepfake videos claiming Ukrainian surrenders or false NATO troop movements. Red teams craft these using AMITT tactics, while blue teams use DISARM Blue to detect and debunk them, testing resilience (Terp & Bouchard, 2019; DISARM Foundation, 2023). In 2022, purple team exercises reportedly identified gaps in detecting Telegram bot campaigns, speeding platform interventions (Atlantic Council, 2022).
Technical-Narrative Integration: MITRE ATT&CK guides purple teams to align cybersecurity with cognitive defences. They’ve tested phishing campaigns delivering disinformation, like fake government alerts, ensuring blue teams block vectors while countering narratives (MITRE, 2023). This layered defence has been critical in Ukraine’s fast-paced information environment.
Rapid Response Calibration: Disinformation spikes during offensives, requiring agility. Purple teams run real-time exercises, simulating false flag operations blaming Ukraine for civilian casualties, sharpening blue team fact-checking and red team anticipation (DISARM Foundation, 2023). These drills have bolstered Ukraine’s ability to counter morale-damaging narratives swiftly.
Community Collaboration: Ukraine’s purple teams often include volunteer tech groups, blending military and civilian expertise. They’ve used AMITT to map propaganda, like bioweapons lab claims, and DISARM Blue to amplify debunking, enhancing trust (Terp & Bouchard, 2019; DISARM Foundation, 2023). This model has exposed foreign influence operations effectively.
These efforts have helped Ukraine counter narratives undermining morale, like false surrender calls, though success depends on speed and public engagement (Atlantic Council, 2022).
The CTI League and Mutton Crew
The CTI League, launched in 2020 to protect healthcare during COVID-19, extended to Ukraine’s disinformation fight post-2022. It used AMITT to map tactics like Spread False Stories, such as Ukrainian war crime claims, and DISARM to guide takedowns, like removing propaganda from platforms (CTI League, 2020; DISARM Foundation, 2023). MITRE ATT&CK secured networks against malware amplifying narratives, like ransomware targeting media (MITRE, 2023).
There are clear links between the operatives of the CTI League to the Mutton Crew, a term for alleged actors targeting citizens with influence operations. Critics tie this to the CCDH’s 2021 Disinformation Dozen report, naming twelve anti-vaccine figures, some later vocal on Ukraine, leading to platform actions (CCDH, 2021). There is a growing body of evidence that confirms the Mutton Crew as a CTI League alias or partnership, and its secrecy fuels speculation of overreach, with the CCDH report seen as targeting lawful dissent (Greenwald, 2021).
Defenders argue the League protected systems, using AMITT to trace coordinated campaigns, not individuals (CTI League, 2020). Yet the CCDH report’s fallout, amplified by governments, sparked perceptions of citizen targeting when platforms censored accounts without clear violations (Greenwald, 2021).
Sara-Jayne Terp’s Role
Sara-Jayne Terp, a cognitive security innovator, co-created AM!TT and shaped DISARM, adapting MITRE ATT&CK for influence operations. In Ukraine, her frameworks guided CTI League efforts to trace disinformation, like false refugee crisis claims, informing blue team responses (Terp & Bouchard, 2019). DISARM’s Red-Blue split enabled simulations, with purple teams testing scenarios like hacked news sites (DISARM Foundation, 2023). Critics argue her tools, used by NATO, risk narrative control, especially when linked to the CCDH report (Greenwald, 2021). Terp insists her focus is resilience, but debate persists (Terp, 2022).
Ethical Crossroads
Fighting disinformation with disinformation is a dangerous game, one that promises nothing but disaster. The CTI League’s alleged connections to the Mutton Crew and the fallout from CCDH stand as clear warnings. Labelling citizens as threats under the guise of protection risks stifling free speech, a reality painfully evident in Ukraine, where dissenters were targeted and scrutinized (Greenwald, 2021). While purple teams in Ukraine work transparently to strengthen defenses, the lack of transparency elsewhere only fuels distrust and suspicion (Atlantic Council, 2022). Tools like AMITT, MITRE ATT&CK, and DISARM equip teams to fight back, and Terp’s work proves their potential. But when defence tactics mirror those of our adversaries, the line between safeguarding and controlling becomes dangerously thin. In Ukraine, purple teams have fortified defences, but it’s not just the tactics that matter, it’s the trust that drives success.
Trust is the true foundation of victory.
The CTI League and the Mutton Crew have shattered our trust in medical establishments, the military and our governments.
Their actions have undermined everything they claimed to stand for.
When countering lies with lies becomes standard, what moral cost do we pay to win the information war?
The sentiment inspector is here to find out.
References
Atlantic Council. (2022). Ukraine’s Cyber Resilience in the Face of Russian Aggression.
https://www.atlanticcouncil.org/
Bellingcat. (2022). Investigating Disinformation in Ukraine’s Conflict.
https://www.bellingcat.com/
Center for Countering Digital Hate (CCDH). (2021). The Disinformation Dozen.
https://www.counterhate.com/
CTI League. (2020). CTI League Mission Statement.
https://ctileague.com/
DISARM Foundation. (2023). DISARM Frameworks Documentation. https://github.com/DISARMFoundation/DISARMframeworks/tree/main/DISARM_DOCUMENTATION
Greenwald, G. (2021). The CCDH Report and Its Implications. Substack.
MITRE. (2023). MITRE ATT&CK Framework.
https://attack.mitre.org/
Terp, S. (2022). Building Resilience Against Misinformation. Medium.
https://medium.com/
Terp, S., & Bouchard, P. (2019). AMITT: A Framework for Misinformation.
https://www.misinfosec.org/